I found an LFI, now what?
Local File Inclusions (LFIs) allow an attacker to include arbitrary files on the victim machine. These files are interpreted as being part of the current page, interpreted as code and returned to the user.
Consider this php snippet which is vulnerable to an LFI attack:
if (isset($_GET['page'])){
include($_GET['page'] . '.php');
}
Once an LFI has been found a common technique is to include user supplied files to compromise the server. This can be done via an array of methods such as including access logs, user sessions, etc.
Here, we will focus on using the LFI to read current php files and enumerate more information about the server. An issue with using LFI to achieve this is the included files will be interpreted – not displayed, so we can’t simply view their source.
Since php 5.0.0+ there is a handy wrapper function we can use to bypass this restriction:
By using a conversion filter, we can base-64 encode a file which will then be included, instead of being interpreted by the php engine. This can be done using the example query string:
php://filter/convert.base64-encode/resource=../../example.php
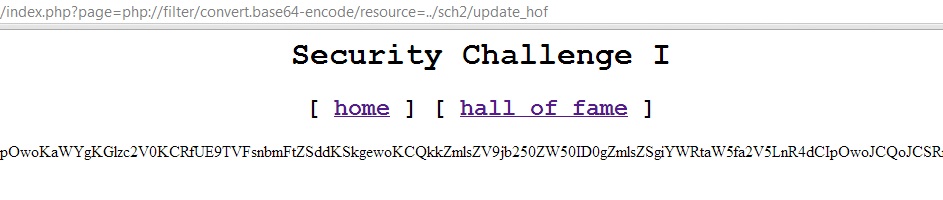
As a worked example we can look at a hacking challenge provided by damo at http://damo.clanteam.com/sch2/, by using an LFI identified in a previous challenge we can use a wrapper method to include an arbitrary php file on the server:
http://damo.clanteam.com/sch1/index.php?page=php://filter/convert.base64-encode/resource=../sch2/update_hof
By decoding the base-64 representation of the original source of the update_hof.php file, we can view the useful configuration information required to solve this challenge.