Why come inside, if I can stand out front?
A busines’ wireless access points offer the potential as a simple vector for network ingress by an attacker. They don’t require specific vulnerabilities, physical access or end user engagement.
All that is required is poor security configuration - either via the employed encryption standard or associated passwords.
The 3 broad access control mechanisms utilised today are:
- None - wherein any user can connect to the network
- WEP - which has been insecure since 2001; and
- WPA - which is vulnerable to dictionary based attacks that is offered as a service at many websites
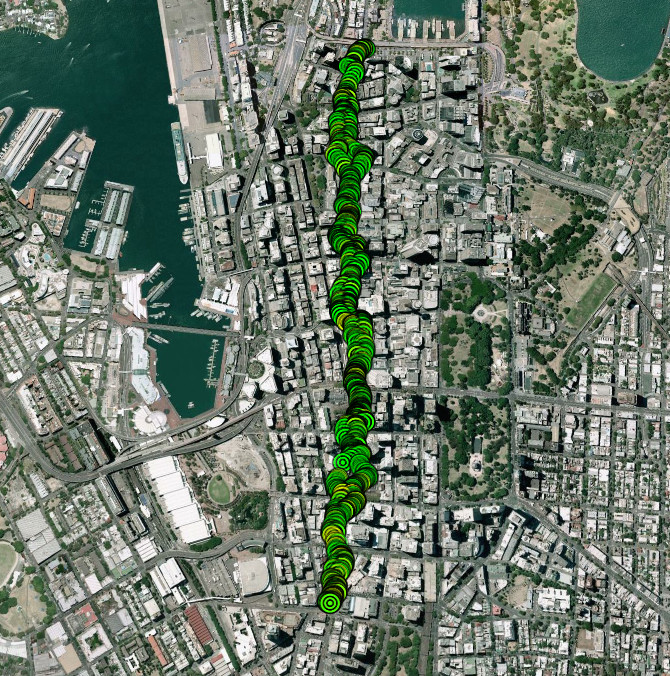
What follows is a general wireless analysis of Sydney’s George Street.
1,514 total unique access points were discovered:
| None | 187 |
| WEP | 65 |
| WPA | 1,262 |
While the open access points need to be taken with a grain of salt (often intentionally open and guest networks), there is a subtle security concern associated with these networks - if your business blocks access to certain sites, a user can trivially bypass this control by connecting to an open network, downloading a potentially (or forced via man in the middle) harmful file and then reconnecting to the corporate network - introducing blocked resources into the environment.
Similarly WEP (particularly) or WPA can introduce a false sense of security at your corporate perimeter, where a WEP or WPA key can be cracked, guessed or read (yes, we can all seen the yellow post-it notes) - unpatched internal systems can be used as pivots to further explore your network and systems.
The most active access points (based on active connections) were:
| Rank | Encryption | Total |
|---|---|---|
| 1 | WPA | 31 |
| 2 | WPA | 23 |
| 3 | None | 23 |
| 4 | None | 22 |
| 5 | None | 20 |
| 6 | None | 19 |
| 7 | None | 19 |
| 8 | None | 18 |
| 9 | None | 18 |
| 10 | None | 17 |
The distribution of WPA protected access points (with names intentionally removed) can be seen below (similar diagrams for WEP and open networks will not be published):
This analysis has shown that while 83% of access points are protected by strong access control mechanisms, some 17% are still utilising legacy or no protection - which while insecure in themselves, can also introduce vulnerabilities into your network by geographical association.