The friendly phisherman
While technical resilience to security can be quantitatively tested and evaluated at some point in time. The human factor is often a weak point which is difficult to assess, even more difficult to rely upon (consistently) and can result in compromise even where technical issues have been addressed.
A simple way to test organisational resilience or the effectiveness of staff security awareness training is to perform social engineering exercises. While areas such as physical access, cold drops and phone calls all fall under this remit (among others), this post will focus on a technique with a very low barrier of entry and expertise – phishing.
So, how can we test an organisations resilience to a phishing campaign?
Launch one.
Our friendly (note step 3) phishing campaign will comprise of 3 simple steps:
- Obtain email addresses for some company (target)
- Send an email to each address containing a uniquely identifiable URL (phish)
- Record which users follow the offending link (log)
To record which user has followed our phishing links, we will send URL’s with the following format:
http://yoursite.com/index.php?id={base64_encode(target email)}
Let’s start by setting up our logging script.
Using php we want to unencode the user’s email address from the $_GET['id'] parameter and log the result to a text file:
<?php
$id = base64_decode($_GET["id"]);
$date = date('d/m/Y h:i:s a', time());
$data = $id . "\t" . $date . "\n";
file_put_contents("log.txt", $data, FILE_APPEND);
?>
We will also add some html so as not to arouse too much suspicion:
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
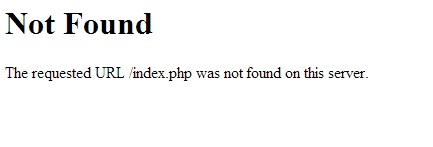
<h1>Not Found</h1>
<p>The requested URL /index.php was not found on this server.</p>
</body></html>
Any user who follows our link will be served a 404 page (note a 302 would work just as well), while their details are logged in the background:
Next we need a list of target email addresses for some given domain, for our purposes we will use theharvester tool, which we will call from our python script:
# harvest $emails_to_send emails for $domain using theharvester with google as source
def theharvester():
return check_output("theharvester -d " + domain + " -b google -l " + emails_to_send + " | grep @" + d, shell=True)
To make our links appear less suspicious we will utilise the free bit.ly url shortening service, (requires account registration to obtain an api key):
# shorten some link u with bit.ly, return shortened url
def bitly_shorten(u):
url = "http://api.bit.ly/v3/shorten?login=" + bitly_user + "&apiKey=" + bitly_api + "&longUrl=" + u + "&format=txt"
return urlopen(url).read()
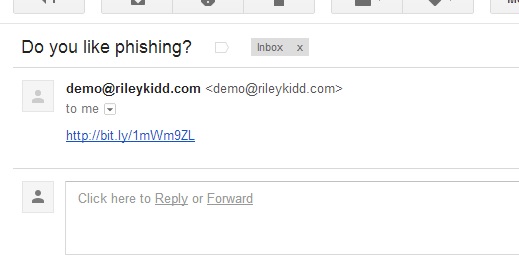
Once we have our list of targets we email each user with our enticing phishing email, they will then receive a custom email in their inbox:
Each user who follows the link will then have their email address logged:
Using this method, we can easily and automatically identify users who are more likely to succumb to a real phishing attack and update staff awareness training as appropriate.
A full python code listing can be found below:
from urllib2 import urlopen
from subprocess import call, check_output
from base64 import b64encode
bitly_user = ""
bitly_api = ""
from_email_account = ""
domain = ""
emails_to_send = ""
log_location = ""
# shorten some link u with bit.ly, return shortened url
def bitly_shorten(u):
url = "http://api.bit.ly/v3/shorten?login=" + bitly_user + "&apiKey=" + bitly_api + "&longUrl=" + u + "&format=txt"
return urlopen(url).read()
# harvest $emails_to_send emails for $domain using theharvester with google as source
def theharvester():
return check_output("theharvester -d " + domain + " -b google -l " + emails_to_send + " | grep @" + d, shell=True)
# send some email from $from_email_account to some email e with some message m
def send_email(e, m):
return check_output("sendemail -f " + from_email_account + " -t " + e + " -u 'Do you like phishing?' -m " + m, shell=True)
for email in theharvester().split():
link = bitly_shorten(log_location + b64encode(email))
print "[+] Phishing " + email + " with url " + link
send_email(email, link)